Azure MFA: Twice MFA for MAC Users
We have deployed the Microsoft Azure MFA in the customer infrastructure. Everything was working fine. MAC users reported Twice MFA. Let us see how did we fix it.
Azure MFA is working as expected. Users will accept and will agree to follow all the steps if it is a security requirement.
At the same time, twice MFA within few seconds can be annoying and frustrating for the users.
Issue:
Azure MFA is working as expected for the users on windows computers and tablets. MAC users were getting 2 MFA phone, txt or app verification prompts.
Resolution:
-Issue looked little strange so reported this to Microsoft.
-Microsoft recommended checking if there are 2 authentications coming to the Azure MFA.
-Logged in to the Azure MFA server and went to the following path
“C:\Program Files\Multi-Factor Authentication Server\Logs”
-Open the MultiFactorAuthRadiusSvc.log file
-2 login request came as shown below.
2017-02-14T02:57:19.234778Z|0|1412|6452|pfrad|Calling pfAuthUser(‘Domain\pnigam’, ”, 1)
2017-02-14T02:57:24.600871Z|0|1412|6452|pfrad|authResult = 1
2017-02-14T02:57:24.600871Z|0|1412|6452|pfrad|rawCallStatus = 21
-This clarifies that there is no bug or issue, in fact, there are 2 authentication requests are coming.
-Yes, on MAC, there was no direct RDP happening and there is no way to do it. When I continue to stare my MacBook 12″. I was able to see 2 logins were happening.
-For customer and me the issue stands the same, users won’t like to do MFA twice within few second.
-The workaround to avoid the multiple logins in quick time is to add cache entry in the Azure Portal by following the below-mentioned steps from here.
- Log on to http://azure.microsoft.com
- Navigate to the MFA Management Portal as per this link. https://msexchangeguru.com/2017/01/16/unable-to-download-azuremfa/
- Click Caching under the Configure section, in the Azure Multi-Factor Authentication Management Portal.
- On the Configure caching page click New Cache
- Select the Cache type and the cache seconds. Click create.
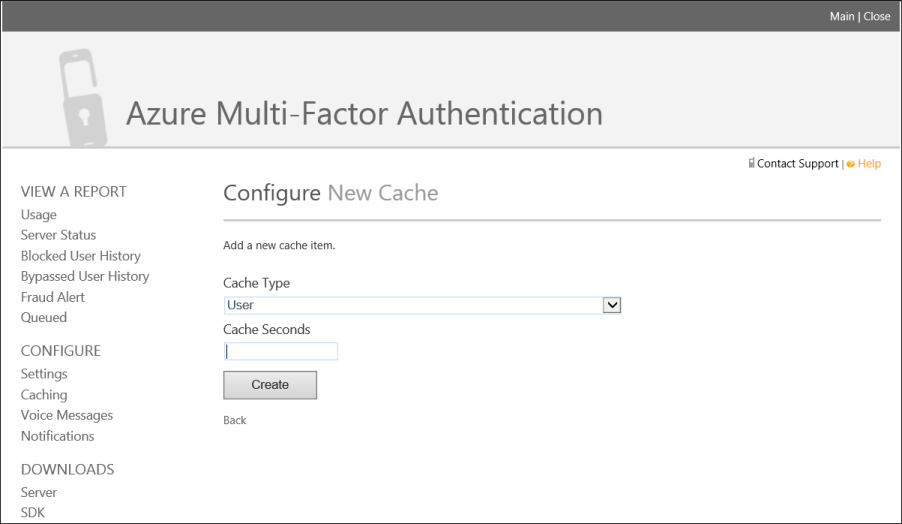
-After configuring the cache, user was prompted only once.
-Checked the MultiFactorAuthRadiusSvc.log file
2 login were coming but they had different rawCallStatus. First one had rawCallStatus = 21 and Second one had rawCallStatus = 6
2017-02-14T02:57:56.986251Z|0|1412|10088|pfrad|Calling pfAuthUser(‘Domain\pnigam’, ”, 1)
2017-02-14T02:57:57.550306Z|0|1412|10088|pfrad|authResult = 1
2017-02-14T02:57:57.550306Z|0|1412|10088|pfrad|rawCallStatus = 6
-Let me decode the code. The below table tells the code description. 21 is Mobile App Authenticated and 6 is Used Cache. Which was just perfect. This table can be very useful in troubleshooting for the security team.
| Code | Description |
| 1 | PIN Entered |
| 2 | No PIN Entered |
| 3 | # Not Pressed After Entry |
| 4 | No Phone Input – Timed Out |
| 5 | PIN Expired and Not Changed |
| 6 | Used Cache |
| 7 | Bypassed Auth |
| 8 | Used Cache |
| 9 | Used Cache |
| 10 | Call Disconnected |
| 11 | Call Timed Out |
| 12 | Invalid Phone Input |
| 13 | Got Voicemail |
| 14 | User is Blocked |
| 15 | Status Pending |
| 16 | Voiceprint Succeeded |
| 17 | Voiceprint Enrolled |
| 18 | Voiceprint Expired and Not Changed |
| 19 | Text Message Authenticated |
| 20 | Text Message Sent |
| 21 | Mobile App Authenticated |
| 22 | OATH Code Pending |
| 23 | OATH Code Verified |
| 24 | Fallback OATH Code Verified |
| 25 | Fallback Security Questions Answered |
| 100 | Invalid Phone Number |
| 101 | Auth Already In Progress |
| 102 | Phone Unreachable |
| 103 | International Calls Not Allowed |
| 104 | PIN Mode Not Allowed |
| 105 | Account Locked |
| 106 | Invalid Message |
| 107 | Invalid Phone Number Format |
| 108 | User Hung Up the Phone |
| 109 | Insufficient Balance |
| 110 | Phone Extensions Not Allowed |
| 111 | Invalid Extension |
| 112 | Fraud Code Entered |
| 113 | Rollover Not Allowed |
| 114 | Return PIN Mode Not Allowed |
| 115 | Event Confirmation Not Allowed |
| 116 | Invalid Event Parameter |
| 117 | Unable to Place Call |
| 118 | Voiceprint Failed |
| 119 | Voiceprint Mode Not Allowed |
| 120 | Text Message Could Not Be Sent |
| 121 | No Text Message Reply Received |
| 122 | Text Message OTP Incorrect |
| 123 | Text Message OTP + PIN Incorrect |
| 124 | Text Message Mode Not Allowed |
| 125 | Localization Not Allowed |
| 126 | User Licenses Exceeded |
| 127 | Text Message User Licenses Exceeded |
| 128 | Voiceprint User Licenses Exceeded |
| 129 | Mobile App Denied |
| 130 | Mobile App Invalid PIN |
| 131 | Mobile App PIN Not Changed |
| 132 | Fraud Reported |
| 133 | Mobile App No Response |
| 134 | Mobile App Mode Not Allowed |
| 135 | Mobile App All Devices Blocked |
| 136 | Mobile App Notification Failed |
| 137 | Mobile App Invalid Result |
| 138 | OATH Code Incorrect |
| 139 | Duplicate OATH Code |
| 140 | OATH Code Out Of Date |
| 141 | OATH Token Mode Not Allowed |
| -100 | Skipped Call |
| -101 | User Not Found |
| -102 | User Disabled |
| -103 | User Incomplete |
| -104 | Trusted IP |
So, we implemented this workaround but we ensured to add the Authentication Type, Application Name, and IP so that the cache only applies to the same IP.
CTO @ Golden Five
Team@MSExchangeGuru


