PST Accelerator – Review
I am a great lover of the Exchange 2010 Personal Archive Mailbox feature. If for no other reason than it makes a tedious task.. well, simple. Here I will be reviewing the best product on the market (a life saver) for migrating your PST files into them, or other technologies.
The product is called PST Accelerator (http://www.pstaccelerator.com). In simple terms it is a product that will discover PST files on your network, report on the health and status of those files, and migrate them to end target technologies like Exchange mailboxes, Exchange 2010 Personal Archive mailboxes, or Enterprise Vault. The interface is well laid out and offers rich information at-a-glance.
Before I proceed – Please use “MSGURU” code if you are contacting them simply for the fact that I need to let them know that you read about the product on MSExchangeGuru… 🙂
Let’s look at some reasons for why PST files should be eradicated in the first place …
Why you shouldn’t use PST files:
It has been quoted in numerous articles in the past that in excess of 70% of an organisations intellectual property is contained within email. While this is a great reason for organisations to employ an email archiving solution like Exchange 2010 Personal Archive Mailboxes, what many organisations fail to do, is manage the ever increasing PST file estate. Here are a few reasons why PST files fail within the enterprise.
Retrieval:
This is one of the biggest concerns with the PST files. After months or years of adding data to PST files, one day you will want to retrieve an email from them only to find that the file has become corrupt or you find yourself having to add many files and search within their folders to find a single email. This is a waste of precious time, or a loss of data.
Security:
The security aspect is a critical issue with PST files. PST files can contain a huge volume of information as stated above. The down side is that there is no way to truly secure them properly. There are hundreds of tools on the market for removing passwords from them all over the Internet. They were never designed to be secure repositories for data, and definitely not an archive strategy for email.
Network Access:
Microsoft has many articles about the fact that PST files are not supported over a LAN/WAN. Many of which have been recently updated to reflect the introduction of Exchange 2010 Personal Archive Mailbox as an alternative to PST files. Simply put, PST file access over a LAN/WAN is common because users feel that putting a PST file on a server ensures they are getting backed up. This leads to an increased likelihood of corruption. Not to forget that the data is only accessible when connected to the location of the PST file, and it slows Outlook performance down immensely.
Backup:
Backing up PST files as a safety measure, unfortunately, usually ends as a story of woe. PST files don’t report that they are corrupt often, so users carry on adding data to an already corrupt store. Backing up a corrupt version of a file won’t save that data. Sometimes being able to get an older version of a PST will get past the corruption, but the data added since corruption is often lost, without the intervention of third party tools, but why take chances with your data?
My most underrated statement: PST files are not meant for archiving your important data!!
Compliance, litigation, regulation and discovery are just a few words we see thrown around regarding email and messaging systems these days. PST files fly directly against the grain of these overwhelming (and often expensive) terms. PST files make discovery a nightmare not only for the end users, but the governance you may have in place.
PST Accelerator helps to eradicate these headaches – and more – through some key features.
-
Fast and accurate discovery of PST files with data ownership and file health reporting.
-
Highly configurable and intuitive interface allowing you to migrate data the way you want to.
-
Accurate and easily digestible reporting that gives you full visibility of how your project is progressing.
-
And many more..
Additional Features:
RCA : PST File migration and eradication is notoriously painful, and often put into the ‘too hard’ basket and ignored. Issues do, and will appear with any migration, but being able to determine the problem is critical to resolving it. PST Accelerator gives rich reporting down to individual item failures for migrations into Microsoft Exchange. Reports can be scheduled to Service desk staff, or technical staff, that list the PST files, the data owner, and errors associated with its migration if desired.
Having a high level over view of your project when needed, and the flexibility to drill down to critical statistics is where PST Accelerator shines.
SMART EFFICIENCY: This is one of my favorite features of the product. Being able to schedule all facets of your deployment from when discovery takes place to when, and how, migration takes place. Being able to modify schedules quickly, and get a graphical overview of your schedules is quick and well organized.
ADMIN EXPERIENCE: The PST Accelerator interface offers a familiar and logical layout. Finding information you need quickly is the very backbone of PST Accelerator.
FLEXIBILITY: PST Accelerator allows almost every facet of your migration to be customized. Taking a project from pilot to a fully automated, install and forget stage is achievable due to the flexibility it offers.
QUOTA MANAGEMENT: Depending on the target for data, you may impact the end users mailbox quotas. PST Accelerator offers the ability to manage the mailbox quotas seamlessly thus reducing calls to service desk.
USER EXPERIENCE: Managing end user communications is often the sticking point for projects. PST Accelerator gives you the ability to schedule end user communications and notifications if desired. The eradication of PST files over all, enables users to seamlessly access their archived information through your archiving technology and strategy.
Eradicating PST files from the enterprise is no longer a painful and complex project that should be ignored. PST Accelerator makes the process straightforward while keeping you informed.
Let’s take a look at the product and the process of getting it deployed …
PST Accelerator Outline
PST files have had their day in the enterprise, and have very few real world reasons to exist any more. The risk of corruption, loss of data, the weakness of the password algorithm used to protect the data on those that are password protected, and the age old “unsupported over a network drive” articles that Microsoft themselves promote, leaves little cause for them to exist. Mix those reasons with the Archiving technologies available today, and the reasons just fall away entirely.
Amongst the obvious reasons surrounding the need to eradicate PST files from the enterprise, are litigation, regulation and compliance. These alone should be sufficient to ring alarm bells for organisations that carry on allowing users to use PST files.
So, the question is what can you do about them? The answer is to either migrate them to Exchange 2010 Personal Archives, back to primary mailboxes, or other archiving technologies like Enterprise Vault with PST Accelerator!
How it works:
PST Accelerator has been designed to operate in a distributed environment. To achieve this, the application has been split into a number of key components: the Central Application and Remote Agents.
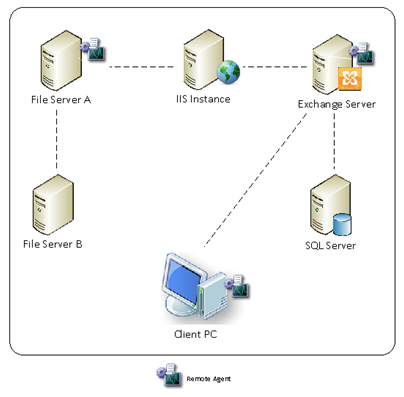
Figure 1 – Schematic overview of PST Accelerator deployment
Central Application
The central application is comprised of a number of distinct technologies:
Database – The database contains the remote file list and history, as well as settings that allow PST Accelerator to operate.
Web Application – The web application presents the screens that permit the Administrator to manage the application and initiate discovery and ingestion functions. For smaller deployments, the web application would generally be installed on an existing Client Access Server; however it can also be deployed onto a shared IIS or dedicated Windows™ server instance. The IIS Instance in Figure 1 shows this. The web application includes a number of web-services that are consumed by the remote agents.
Remote Agents
The remote agent is a Windows service that is delivered as a self-contained MSI package, allowing it to be deployed manually or automatically via, for example, Microsoft™ SCCM. One or more remote agents are installed into the enterprise and then configured to perform a selection of distinct roles via the central application:
Discovery – Network bandwidth and infrastructure limitations are taken into account when deploying the remote agents for discovery purposes. The discovery process trawls the file system in order to identify PST files. This can be very IO intensive and it is recommended that one remote agent is deployed onto each file server. This not only optimises disk access, but also minimises network traffic between the remote agent and the file system.
Where the remote agent cannot be installed onto the target server, the remote agent can be deployed onto a nearby server and configured for remote scanning. File Server A and File Server B in Figure 1 show this.
In some instances it may be desirable to configure the Microsoft Exchange™ installed remote agent to perform remote scans as well as the ingestion function.
Ingestion – At a minimum, one remote agent must be installed onto each Exchange Server™ that homes mailboxes, in tandem with Microsoft Outlook 2007 (SP2) or later so that the ingestion process is able to operate.
This document outlines a high level overview of PST Accelerator® in a Microsoft Exchange Server ® enabled infrastructure.
Minimum system requirements
The following minimum pre-requisites must be installed In order to successfully install and run PST Accelerator:
- Windows Server 2003
- IIS 6
- .NET 4
- SQL Server 2005 (Or SQL Express)
- Microsoft Exchange Server 2003
- Kerberos authentication
- Sufficient storage on the Microsoft Exchange™ server for the migrated PST Files
It should be noted that these are the minimum system requirements and indicate the earliest versions of software supported.
NOTE: For the migration of PST files, PST Accelerator requires Microsoft Outlook 2007 or later to be installed on any Microsoft Exchange Mailbox Servers that home mailboxes where PST files will be migrated to. This is possible due to the Microsoft compatibility guide.
Information required before starting installation
The following information will be required before starting the installation:
- The PST Accelerator installation files
- The name and password of a service account with sufficient permissions to access all PST files, and access mailboxes within the Exchange Organisation.
- The name of the server / instance of a SQL Server.
Installation Overview
Installation of PST Accelerator takes place in a number of stages, as summarised below:
- Apply Exchange security settings for access to mailboxes.
- Install the SQL Database and set database security
- Create an IIS website
- Deploy the Remote Agent
- Install Microsoft Outlook 2007/2010 on Microsoft Exchange Server(s) that home mailboxes.
The above points are described in detail within the Installation Guide provided with PST Accelerator source files, including a breakdown of change requests that would typically be needed for organizations following ITIL best practices.
Once the installation has been performed successfully, PST Accelerator can be managed through the IIS Website created.
The Interface:
PST Accelerator allows administrators to manage their PST eradication project through a web interface that has been designed to offer a logical and intuitive flow to the management of your project.
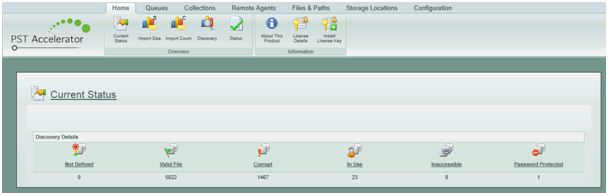
Once PST Accelerator has been deployed and the licence applied, the interface shown in Figure 2 is displayed showing the number of files discovered, broken down into queues that give an overview of potential issues that could hinder the progress of the PST eradication project. Further details of the PST file estate can be gained from the available reporting pages as shown in Figure 3.
Reporting:
Having accurate reporting is essential to gaining an overview of the progress of your PST eradication project. PST Accelerator offers detailed and informative up-to-date graphs and data. When encountering issues with a file, it is important to be informed of the cause, PST Accelerator allows you to drill down to the log file of the file and analyse when and why the file migration failed.
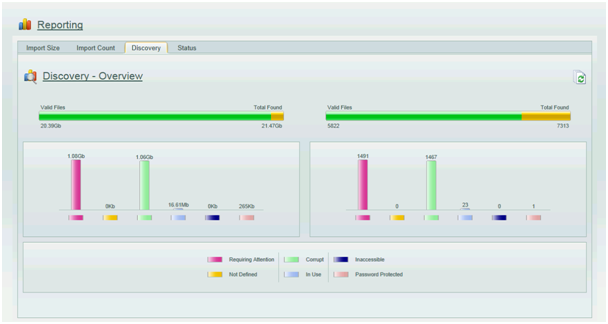
Figure 3 shows further detail of the volume and count of PST files discovered, and displays them based on their discovery status. It should be noted that the discovery status has no bearing on the migration status of a file as their condition may change between the time of discovery and migration.
PST Files that have been discovered can be further analysed within the Queues tab. Here, analysis of the individual files can take place. You can search for files based on many criteria, sort, or arrange that information, and gain access to the current status of the file. Figure 4 shows the status of a file that has been partially migrated, while Figure 5 shows a file that has been successfully migrated.
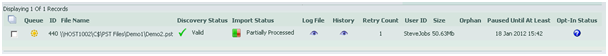

As displayed in both Figure 4 and Figure 5, a great deal of information can be gained from these entries such as the health of the PST file when it was discovered, the number of attempts it took for the file to be successfully migrated, the size of the PST, the owner of the file, and much more. The path to the PST file, log file and history items are all hyperlinks which link to further information about the file and its status.
Knowing how the project is going is critical to its success. PST Accelerator offers at-a-glance information that helps you determine how the over all project is progressing, including more granular details right down to individual files. Figure 6 shows statistics about the migration of the PST estate including the average processing time of a PST file, giving you an indication of how long your project may take given the number of files. It is essential to take into account factors like scheduling, and PST files that require more than one attempt to migrate successfully when calculating project duration.
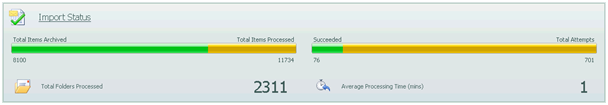
The configurability of the PST Accelerator gives you control of where and when discovery takes place. This can be performed as a blanket approach, or with defined paths and computers.
Having the flexibility to schedule tasks like discovery and migration makes dealing with time zones or departments manageable around their requirements and that of the project.
Scheduling:
PST Accelerator allows administrators to schedule events at times when tasks are most productive, and don’t conflict with other activities like backup schedules or server patching. Schedules are available at a glance and are shown graphically per agent or globally as shown in Figure 7.
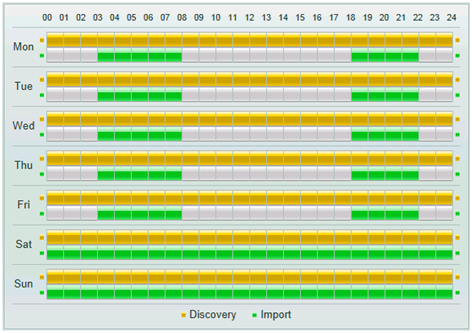
Figure 7 above, shows a schedule for a remote agent that is enabled for discovery 24/7, but is only enabled for migration at selected times during weekdays, and all day at weekends.
Remote Agents:
PST Accelerator functions based on remote agents. Remote agents can be deployed manually through the PST Accelerator web interface, or via deployment tools such as SCCM.
A remote agent can be configured to perform local discovery, remote discovery or migration. Any combination of these tasks can be assigned to a remote agent, and an overall status of deployed remote agents can be seen through the Remote Agents reporting page.

Figure 8 shows three remote agents that have been deployed. Their status and assigned tasks are shown in the columns aligned to the server name they are deployed on. Tool tips are available by hovering the icons shown in the web interface. Below is a legend explaining their purpose.
 This displays if the remote agent is set as Active.
This displays if the remote agent is set as Active.
 This shows if the remote agent is within a schedule.
This shows if the remote agent is within a schedule.
 This indicates if the remote agent has communicated back to the central service.
This indicates if the remote agent has communicated back to the central service.
 This indicates the time – in minutes – that the remote agent differs form the central Service.
This indicates the time – in minutes – that the remote agent differs form the central Service.
 This indicates if the remote agent is enabled for PST Import.
This indicates if the remote agent is enabled for PST Import.
 This indicates if the remote agent is enabled for local scanning.
This indicates if the remote agent is enabled for local scanning.
 This indicates that the remote agent has remote file scanning enabled.
This indicates that the remote agent has remote file scanning enabled.
Migration:
Migration of PST files is what PST Accelerator is designed to do. No two PST eradication projects are the same, and often no project finishes with the same requirements it started with. PST Accelerator gives you the flexibility to accommodate changes easily.
There are many factors that influence a PST eradication project, from end user communication, mailbox quota management and end user experience. PST Accelerator allows you to configure all of these and much more.
Educating users effectively can often be one of the most important factors of the project. PST Accelerator manages communication without bombarding your user. These communications are fully customizable in plain text or HTML. Further communications can also be configured and scheduled to be sent to service desk staff listing PST files and their owners that have snagged the project. Thus giving you the upper hand when needing to manage expectations and issues.
Not all users are treated the same, and some require special attention. PST Accelerator gives you the ability to quickly manage users who require their files migrated out of schedule. PST Accelerator allows you to set files to migrate regardless of migration schedule if needed, thus for users who are in a rush, using our Run Now queue manages these users while giving them the full project experience with communications, and the same end user experience as scheduled users.
There are ever increasing reasons to eradicate PST files from your enterprise appearing every day, and PST Accelerator is listening to those reasons and building our product to accommodate more archiving technologies and allowing more flexibility around what we’re hearing in the enterprise.
PST Accelerator offers a FREE discovery license which can be used to find your PST files and highlight just how big a problem exists in your enterprise. From there, we’re happy to talk to you about the options you have around your migration policies and techniques.
Contact us today on sales@pstaccelerator.com or visit at http://www.pstaccelerator.com
Ratish Nair
MVP Exchange
Team@ MSExchangeGuru



February 7th, 2012 at 6:26 pm
PST Accelerator- The reporting looks awesome… Will check it out…