SMTP Relay connectors in Exchange 2016
As we all know A Receive connector is responsible for all SMTP inbound connections from an external source, client/partner or another Exchange server.
Receive connector accepts the inbound connections as per the configuration and each Receive connector on the Exchange server uses a unique combination of local IP address bindings, TCP ports, and remote IP address ranges.
Exchange 2016 servers use Receive connectors to control inbound SMTP connections from:
- Messaging servers that are external to the Exchange organization.
- Services in the transport pipeline on the local Exchange server or on remote Exchange servers.
-
Email clients that need to use authenticated SMTP to send messages.
Transport Services on Exchange server 2016:
Exchange 2016 comprises of two server roles called Mailbox server role and Edge Transport server role. A Mailbox server role has three key transport services (substitute role) called transport pipeline as below and the mail flow works through these pipelines.
-
Front End Transport service: Front End Transport service acts as a proxy for all incoming and outgoing (optional) emails. It doesn’t perform any email queuing or an email inspection and does not communicate with mailbox transport service directly. It receives all external SMTP traffic and then sends it to transport service.
-
Transport service (Hub Transport service): Transport service is similar to a hub transport server on exchange 2010, which handles all SMTP mail flow, performs queuing, content inspection and categorization of emails. This service also executes an anti-spam and anti-malware inspection. It receives incoming email from front end transport service and forwards to mailbox transport service.
NOTE: Transport service never communicates directly with mailbox databases.
-
Mailbox Transport service: Mailbox Transport service is the one which stores incoming emails into their respective mailboxes. This service includes:
-
Mailbox Transport Submission service: – Mailbox Transport Submission service will retrieves message from mailbox database using an Exchange remote procedure call (RPC) and delivers them to transport service in order to send emails to respective recipients.
NOTE: The Mailbox Transport Submission service has access to the same routing topology information as the Transport service
-
Mailbox Transport Delivery service: – Mailbox Transport Delivery service accepts the emails from transport service and connects to mailbox database using RPC (Remote Procedure Call) and stores them in the respective mailbox databases.
-
NOTE: The Mailbox Transport service doesn’t connect with Front End Transport service, Mailbox Transport service, or mailbox databases on other Mailbox servers.
Transport service on Edge Transport servers: Transport service on Edge Transport servers is very similar to the Transport service on Mailbox servers. If an Edge Transport server is installed in the perimeter network, mail flow to the Internet flows through the Transport service Edge Transport server.
Default Receive connectors in Exchange server 2016:
When an Exchange server 2016 is installed, default receives connectors will be configured automatically on the mailbox servers and when it is subscribed in Exchange organization on Edge transports servers. These default receive connectors are appropriate for inbound mail flow in most of the cases. On Mailbox servers, the Receive connector is stored in Active Directory as a child object of the server and on Edge Transport servers; the Receive connector is stored in Active Directory Lightweight Directory Services (AD LDS).
There are 5 defaults receive connectors created as below, in which three Frontend Transport receive
connectors and two Hub Transport service connectors.
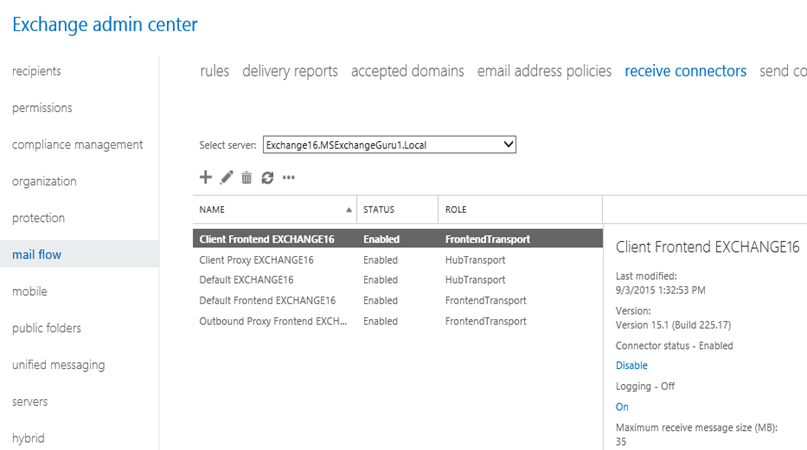
- Client Frontend EXCHANGE16: – Client Frontend EXCHANGE16 connector accepts secure connections, with Transport Layer Security (TLS) applied on the port 587. This is used by IMAP and POP clients. This receives connector proxy’s connection from IMAP and POP applications to Client Proxy EXCHANGE16 which is a Hub Transport receive connector.
- Default Frontend EXCHANGE16: – Default Frontend EXCHANGE16 connectors receives the Emails sent from Internet on port 25 and then send it to Default EXCHANGE16 which is a transport service on Hub Transport on port 2525.
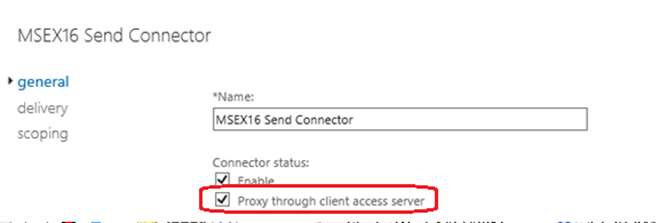
- Outbound Proxy Frontend EXCHANGE16: – Outbound Proxy Frontend EXCHANGE16 receive the outgoing emails on the port no 717, if proxy through client access server option is selected on this Send connector. Or in simple words this connector receives emails sent by the transport service, if proxy through client access server option is enabled in Send connector as shown below.
Client Proxy EXCHANGE16: – Client Proxy EXCHANGE16 is a hub transport service which receives emails sent from frontend services on port 465 and sends to mailbox transport service. This receive connector accepts proxy POP and IMAP connections sent from Client Frontend EXCHANGE16 front end transport connector.
Create a custom Receive connector in Exchange Server 2016:
Though the default Receive connectors are suitable in most cases, we can even create custom Receive connectors for specific situations/requirements:
NOTE: On Mailbox servers, we can use Exchange admin center (EAC) or Exchange Management Shell to create and manage Receive connectors, but on Edge Transport servers, only Exchange Management Shell can be used.
Exchange 2016 Receive connectors has below features in compared to Exchange 2010:
-
The TlsCertificateName parameter allows specifying the certificate issuer and the certificate subject, which helps in minimizing the risk of fraudulent certificates.
-
The TransportRole parameter allows distinguishing between frontend (Client Access) and backend connectors on Mailbox servers.
Open EAC and Navigate to Mail Flow àReceive Connectorsà Click on New :
:
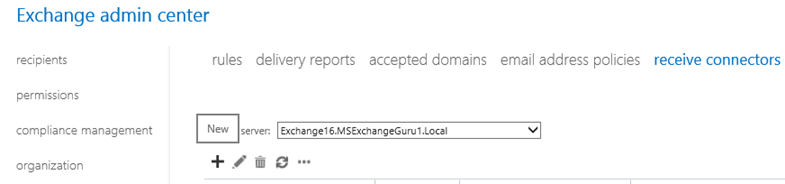
In the new Receive Connector window, provide Name and select Role and the type of Connector and click on next:
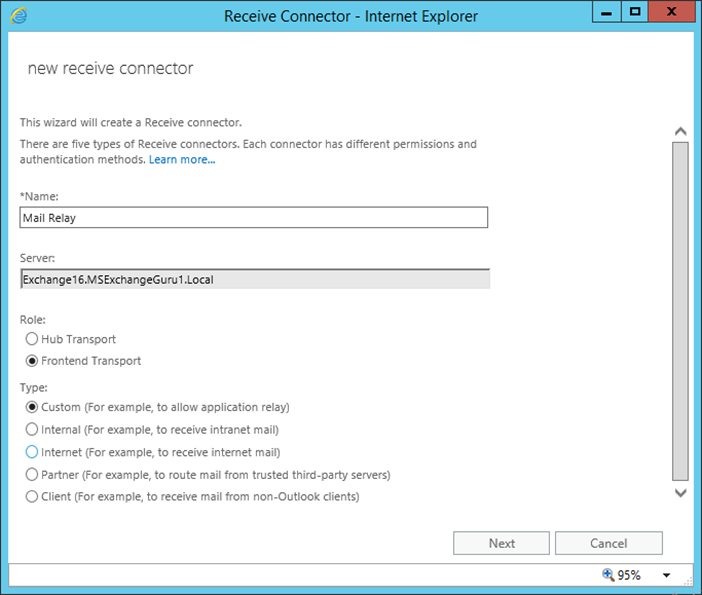
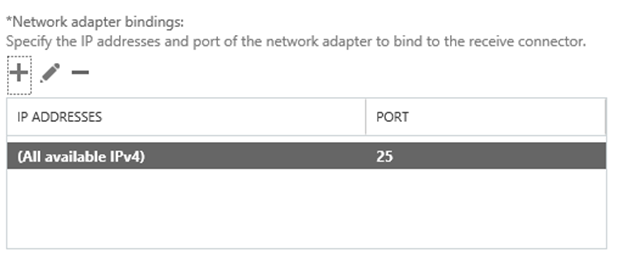
The default Network adapter bindings are okay, just leave it as it is. This is the IP and port on which the server will be accepting the connections.
Multiple receive connectors on the Frontend Transport service can listen on the same port of TCP 25.
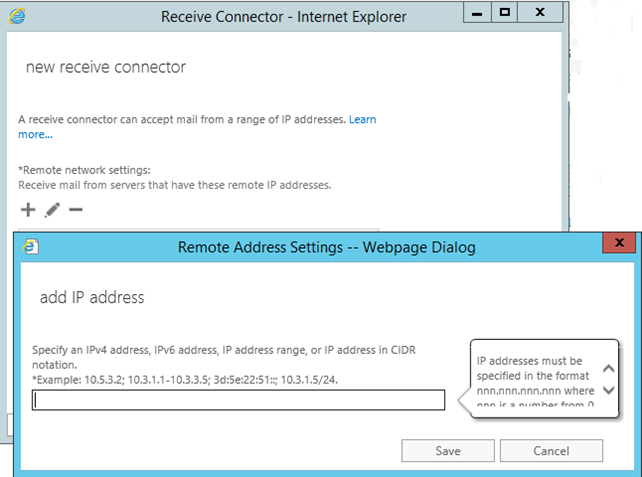
Under Remote network settings, remove the default IP ranges add specific IP addresses or IP ranges that is required to allow anonymous SMTP relay from.
NOTE: It is not recommend adding entire IP subnets as this might cause an issues with server to server communications.
Click on Finish to complete the wizard:
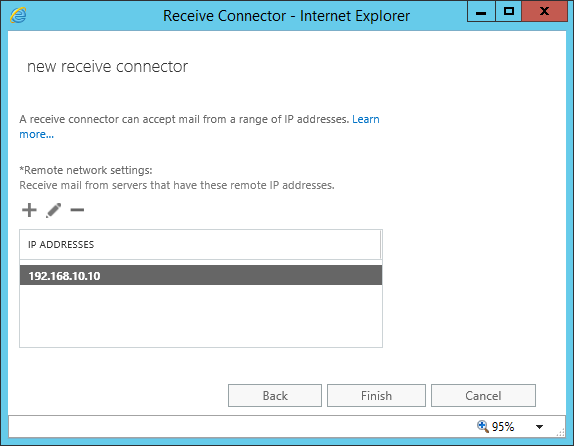
Once the Receive connectors are created, it requires providing the necessary permissions and enable open relay in order to complete the Receive connector creation successfully.
Provide the permissions:
Set-ReceiveConnector “Exchange16Email Relay” -PermissionGroups AnonymousUsers
Enable Open Relay:
Get-ReceiveConnector “Exchange16Email Relay” | Add-ADPermission -User ‘NT AUTHORITYAnonymous Logon’ -ExtendedRights MS-Exch-SMTP-Accept-Any-Recipient
Using PowerShell commands to configure Internal Relay connectors:
Create a Receive connector:
New-Receiveconnector -Name “<Name of the receive connector>” -RemoteIPRange (“<IP address range>”) -TransportRole “FrontendTransport” -Bindings (“0.0.0.0:25”) -usage “Custom” -Server “<Exchange server name>”
Assigning permissions:
Set-ReceiveConnector -identity “<serverreceive connector>” -PermissionGroups “AnonymousUsers”
Enabling Open Relay:
Get-ReceiveConnector “<Name of the receive connector>” | Add-ADPermission -User “NT AuthorityANONYMOUS LOGON” -ExtendedRights “Ms-Exch-SMTP-Accept-Any-Recipient”
Ratish Nair
Microsoft MVP | Exchange Server
Team @MSExchangeGuru


