Install SSL certificate on EDGE Transport server role for TLS
EDGE transport server installation by default comes with a self-signed certificate. If we need to use a certificate issued by an internal windows certification authority server, follow this article.
This article can also be used for securing email communication using TLS for your EDGE transport server.
Run this cmdlet to get details on the cert currently installed on the EDGE server:
Get-ExchangeCertificate |fl
You may see:
IsSelfSigned : True
Issuer : CN=ServerName
This article basically outlines the following steps:
- Create a new CSR (Certificate Signing Request) from Exchange Management Shell
- Take the CSR output to Windows CA (Windows certificate authority) and generate the certificate
- Install the root certificate and the new certificate on the EDGE servers local computer certificate store
- Import the cert to EDGE server
- Assign the cert to SMTP service
- Test to make sure it is valid
Troubleshooting:
Repair a certificate if the private key is missing
Open ports required from the EDGE server to the Windows CA server for Certificate Revocation Check
Create a new CSR (Certificate Signing Request) from Exchange Management Shell
Use the following cmdlet:
New-ExchangeCertificate -GenerateRequest -Domainname NBC-D-EDG01.CONTOSO.PRI -PrivateKeyExportable $True >>c:\CSRreq.txt
—–BEGIN NEW CERTIFICATE REQUEST—–
MAAD1DCCArwCAQAwAjEgMB4GA1UEAwwXmkJDLUQmRUReMDEuQ09OVE9mmy5QUkkw
ggEAMA0GCSqGSAb3DQEBAQUAA4ABDwAwggEKAoABAQDG7lFxw4rVuyVzQ95e99UA
eX3YAmk5Zl9mJfzls7YGysEZAeAzALryyqo1pomyP0CaZqZMzvaAeE5v55PAmecS
FXq3xmcjAO8OKZZqzw6Mb+xFFJ9ak1J07qSRgYAfUaL557KGqDJVJuGDweFzjDAp
GDLSMAYmPWQamMd3d+/AzAe0eagBl5FelFp0Z/LMc0mFjk75+/mjGpWcqB0oe6+X
LjjYq4M0s5VMlV/omrUVSvkEd/BMuVg6XpEMf+y1mB/dddMrXAmPx11ppmABCPgv
35EyddXUMMm9rrxFuraqObdrKAaAfVefMeKz595eAlW5MFPy/qd5y9F+lDM9dYwP
AgMBAAGgggFrMBoGCAsGAQQBgjcMAgMxDBYKMA4xLjc5MDEuMjBMBgkrBgEEAYA3
FRQxWjBYAgEFDBduYmMmZC1lZGcwMS5jb550b3MvLMByaQwWV09SS0dSm1VQXE5C
Qy1ELUVERzAxJAwAmWljcm9zb5Z0LkV4Y5eebmdlLlMlcMZpY5VAb3M0LmV4ZmBw
BgkqekAG9w0BCQ4xYzBeMA4GA1UdDwEB/wQEAwAFoDAABgMVeREEGzAZgedOQkMm
RC1FREcwMS5Dm05Um1MPLlBSSmAMBgMVeRMBAf8EAjAAMB0GA1UdDgQWBBmQd83F
8uE0P4Z6Egm388gkkOAXpmByBgorBgEEAYA3DQACMWQwYgABAR5aAE0AaQBjAeAA
bwBzAG8AZgB0ACAAUgBmAEEAAABmAEMAaABeAG4AbgBlAGwAAABDAeAAeQBwAeQA
bwBMAeAAYQBwAGgAaQBjACAAUAByAG8AdgBpAGQAZQByAwEAMA0GCSqGSAb3DQEB
BQUAA4ABAQA/o3lAj+Edmku/JGmYmejfmAbfOVEgzoQPgecdLCDJKDP3LKAgQpVc
UWPU5rLryMgBQKM1UkmjjPABzmppVyKeMMJYQ3AbsYv8MWlJxw3MejVrARAS7Bsj
WAADMMXJRuemb5ewmkeev7JLMR6qx7eeLwMYY4SXkuxVexqyMemeLe+BgLV8YSdA
qdumALBc1zpmPW8AKJVkgpDCvFMX1MYM5sJDl1XDMVSA5+fdqEmJ5qe/5Kg++kry
yAcaedrMXesAampACXAjoqL14AKYLpMPMkkMMygJr3X/5MbSec/MG5Azmaw3SzRg
PoXeegEwg81pYXxpcfmAMrQ8wEMkM8me
—–END NEW CERTIFICATE REQUEST—–
This is an example CSR you will see.
Take the CSR output to Windows CA (Windows certificate authority)
How to Create a new Certificate using a Windows certification authority
Navigate to your Windows CA server – http://windowsCAserverNameORipAddress/Certsrv
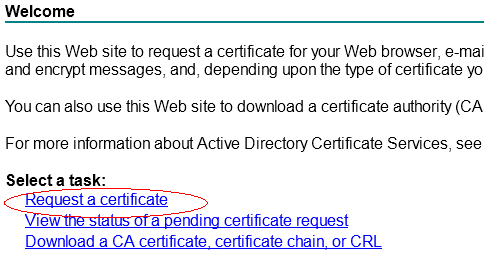
Click Request a cert and then click “Submit an advanced certificate request.”
Now click:
Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file.
Now paste the CSR you got from step one “including” the space at the end
Select web Server as shown in cert template
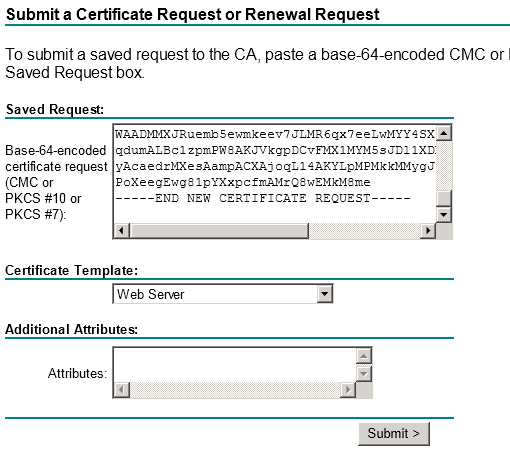
Now click Submit and download the cert in the next screen
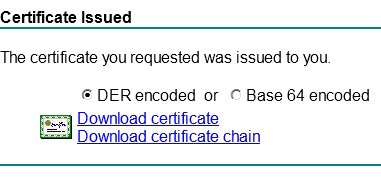
Install the root certificate and the new certificate on the EDGE servers local computer certificate store
Copy the certificate to the EDGE server and double click to open it
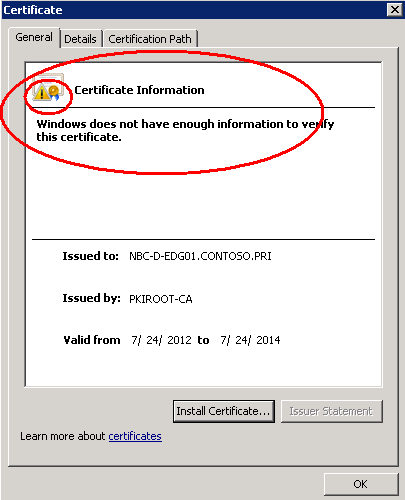
You will see the message, “Windows does not have enough information to verify this certificate”
Now click “Certification path” on the top
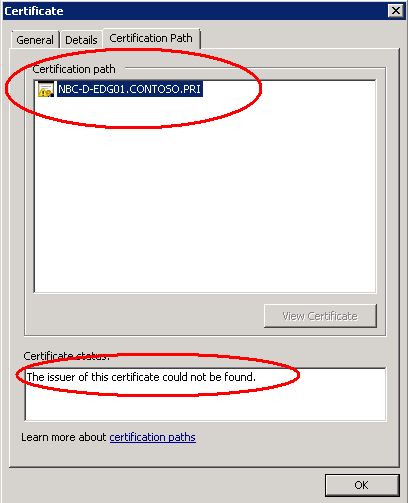
You will see the message, “The issuer of this certificate could not be found”
This is because we DO NOT have the ROOT certificate installed on the EDGE server.
The Yellow exclamation on the certificate name means “I have no clue who issued this certificate”
So let’s install the Root certificate. Navigate to the Windows CA server and get a copy of the Root certificate and Intermediate certificate – if any.
To do this, on the Windows CA server – http://windowsCAserverName/Certsrv
Click
Download a CA certificate, certificate chain, or CRL
On the next page click:
Download CA certificate – If you have a ROOT CA only and no Intermediate CA
Download CA certificate chain – If you have both Root and an Intermediate CA
Now transfer the cert – *.cer or *.p7b depending on the one you downloaded to the EDGE server
Usually the EDGE server maybe in a DMZ which will prevent you to transfer easily. I use Gmail drafts or Microsoft Skydrive to access the certs in all location
On the EDGE server,
Start à Run à mmc
Click File – Add/Remove Snap in
Click Certificates and click Computer Account

Click Local computer and click finish
I usually install the root cert in all 4 locations as shown:
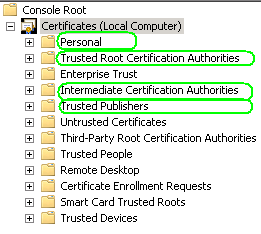
Now, right click each store and click import and import the ROOT cert in all 4 locations.
Remember – If you have an intermediate certificate authority, that certificate should also be installed or your certificate won’t be verified
Also install the EDGE server certificate (NDC-D-EDG01.CONTOSO.PRI) you generated in step 1 to the Personal Store of the server.
Now if you look at the EDGE server certificate, it will look alright:
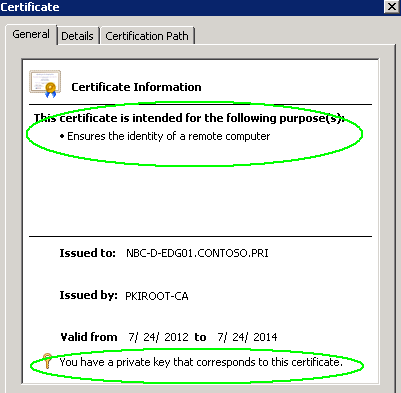
If this cert doesn’t have “You have a private key that corresponds to this certificate”, you will get the error while enabling the certificate in the last step. Let’s cover it right away.
Enable-ExchangeCertificate : The certificate with thumbprint XXXXXXXXX was found but is not valid for use with Exchange Server
(reason: PrivateKeyMissing).
At line:1 char:27
+ Enable-ExchangeCertificate -Thumbprint XXXXXXXXX -Services “SMTP”
Now we need to repair the cert which is a simple process.
Double-Click on the recently imported certificate.
Note: In Windows Server 2008 it will be the certificate missing the golden key beside it. Select the Details tab.
Click on the Serial Number field and copy that string.
Note: You may use CTRL+C, but not right-click and copy.
Open up an elevated command prompt session. (cmd.exe aka DOS Prompt)
Type:
certutil -repairstore my “SerialNumber” (SerialNumber is that which was copied above)
After running the above command, go back to the MMC and Right-Click Certificates and select Refresh (or hit F5 in the MMC)
Double-Click on the problem certificate. At the bottom of this window (General tab) it should state: “You have a private key that corresponds to this certificate.”
Note: In Windows Server 2008 there will be a golden key to the left of the certificate, so there is no need to double-click the certificate.
Now that the Private Key is attached to the certificate, please proceed to enable Exchange Services via Enable-ExchangeCertificate.
Import the cert to EDGE server
Now let’s navigate back to the EDGE server and import this new cert from C:\NBC-D-EDG01.cer
Use the cmdlet:
Import-ExchangeCertificate -FileData ([Byte[]]$(Get-Content -Path C:\NBC-D-EDG01.cer -Encoding byte -ReadCount 0))
If it says the certificate already exists, we can proceed to the next step:
Import-ExchangeCertificate : Cannot import certificate. A certificate with the thumbprint EEFA7LBKJ875897KBKHHKJDRDT3645FYGUBI496D already exists
Enable-ExchangeCertificate -Thumbprint EEFA7LBKJ875897KBKHHKJDRDT3645FYGUBI496D -Services SMTP
CertificateDomains : {NBC-D-EDG01.CONTOSO.PRI}
HasPrivateKey : True
IsSelfSigned : False
Issuer : CN=PKIROOT-CA, DC=contoso, DC=pri
NotAfter : 7/24/2014 10:09:47 AM
NotBefore : 7/24/2012 10:09:47 AM
PublicKeySize : 2048
RootCAType : Registry
SerialNumber : 33G6515E00000000000F
Services : SMTP
Status : RevocationCheckFailure
Subject : CN=NBC-D-EDG01.CONTOSO.PRI
Thumbprint : EEFA7LBKJ875897KBKHHKJDRDT3645FYGUBI496D
As you can see the certificate is now enabled for SMTP service but now we have an issue where Certificate RevocationCheckFailure happened.
RevocationCheck is a check to ensure the EDGE server can communicate with the Windows CA server to verify if the certificate is valid or not.
To resolve this, you need to ensure the EDGE server can communicate with the Windows CA server on ports for Certificate Revocation List traffic:
Firewall rules between the perimeter network and the internal network to contact CRL distribution point to get the certificate revocation list:
-
Server Protocol = LDAP or HTTP or FTP
-
For LDAP: port = TCP: 389, UDP: 389. For HTTP: port = 80. For FTP: Port = 21
Note: The Certificate Revocation List is needed either to validate the client certificate during smart card authentication or when the certificate deployed on RD Gateway is an enterprise/standalone CA certificate. To know which protocol is needed to contact the CRL distribution point for a certificate, open the certificate and go to the Details tab and look at the CRL Distribution Points field.
I got this info from the Remote Desktop services blog
RD Gateway deployment in a perimeter network & Firewall rules: http://blogs.msdn.com/b/rds/archive/2009/07/31/rd-gateway-deployment-in-a-perimeter-network-firewall-rules.aspx
Once you resolve the issue with ports, restart the server and your EDGE server would be ready to accept TLS emails securely.
Ratish Nair
MVP Exchange
Team@ MSExchangeGuru
Keywords: RevocationCheckFailure, Import-ExchangeCertificate : Cannot import certificate. A certificate with the thumbprint EEFA7LBKJ875897KBKHHKJDRDT3645FYGUBI496D already exists, certutil -repairstore my, repair certificate, Enable-ExchangeCertificate : The certificate with thumbprint XXXXXXXXX was found but is not valid for use with Exchange Server (reason: PrivateKeyMissing), You have a private key that corresponds to this certificate, The issuer of this certificate could not be found, Windows does not have enough information to verify this certificate, Install the root certificate, Create a new CSR (Certificate Signing Request),



October 21st, 2012 at 11:58 pm
Very insightful writing on site security with ssl. Thanks, I really walked away more learned than before.
October 23rd, 2012 at 10:56 pm
Excellent knowledge, thanks a lot.
My question is that should we use an external cert for securing email delivery externally (secure SMTP traffic) instead of using an internal cert, in other words, what’s the advantage of using an external cert on edge server?
Thanks again.
October 24th, 2012 at 8:55 am
Thank You Grace !!! well – I dont see any advantage of using a public cert…
October 25th, 2012 at 9:28 pm
Hi Ratish,
I might not express the background of my question with more details previously. Recently, one of our business partners approached us and asked whether our email gateway is TLS capable because they would like to set up secure email gateway to guard against information loss between both.
Regardless what their SMTP system is (might be UNIX, Domino or MS Exchange), we have Microsoft Exchange 2010 with Edge server point to our MailMarshal (used as a smart host) which flow SMTP mail to MessageLab for further SPAM filtering. Currently, we have only used our internal CA issued STARTTLS on EDGEs and HUBs for communication between them.
I am thinking there are few approaches:
1) End-to-End security by using user certificate without doing anything on Edge/External send connector, this requires internal PKI with a kind of Federation trust on both our partner and our ends (Internal domains).
2) Server-to-server security (between our MailMarshal/Edge with TLS capable and our business partner’s SMTP gateway) by implementing TLS on our Mailmarshal and Edge server by using 3rd party certificate (this was where my previous question came from)
So with option 2 above, if we use our own CA to enable TLS on Edge external send connector, would our business partner’s TLS/SMTP gateway accepts our mail or refuse it? Furthermore, will all other non-TLS SMTP domains accept our emails or we should set up two send connectors – one for TLS and another one with non-TLS?
I would think a TLS enabled send connector will negotiate a mutual TLS session with the receiving end first before sending SMTP traffic, if the other end is incapable to do so, then it sends in plain SMTP.
Please advise if my thoughts are wrong. Thank you.
October 29th, 2012 at 9:01 am
Im using internal certs, so it should work fine…
November 9th, 2012 at 9:28 am
[…] Install SSL certificate on EDGE Transport server role for TLS: https://msexchangeguru.com/2012/07/24/edge-server-tls/ […]
January 18th, 2013 at 11:54 am
[…] Install SSL certificate on EDGE Transport server role for TLS: https://msexchangeguru.com/2012/07/24/edge-server-tls/ […]
September 20th, 2013 at 12:44 pm
[…] I would recommend to review this blow to know how to request new cert and review the private key: https://msexchangeguru.com/2012/07/24/edge-server-tls/ […]
September 20th, 2014 at 2:28 am
This web site certainly has all the info I needed concerning this subject and didn’t know who to ask.
January 27th, 2015 at 8:35 am
this site gave me the answer to my question what is great! i give you many thanks and will read you more!
May 5th, 2017 at 8:10 am
Very nice, thank you best regards