Load Balancing Exchange Server 2013 – Good to know stuff
Load Balancing is the distribution of workload across different available servers, so as to accomplish optimal resource utilization, maximized throughput, minimized response time and avoidance of overload. They are referred to as Application Delivery Controller.
With Load Balancing we can increase the capacity by allocating more servers under the load balancing thereby enhancing the traffic handling capacity. This will also result in High availability. When a server failure occurs, the load balancer will redirect traffic to other servers under the load balancer.
SSL Offloading is not supported in Exchange 2013
SSL Offloading is supported in Exchange 2013 post service pack 1. – update 7/4/2014
Additional Options Available Under Load Balancing
-
SSL Offloading- Through SSL offloading, the load balancer will re-crypt/decrypt the SSL traffic from clients. This thus offloads the task of decryption/re-cryption from the application server saving essential application server resources.
-
Maintenance Mode- When a server is marked under maintenance mode, no traffic is sent to that server. This can be particularly useful in cache servers.
-
Caching- Facilitates cache application items that are required frequently eliminating the need to reload them.
-
Compression- Enables traffic Compression
-
Pre-Authentication- As the name suggests, with this option exchange can pre authenticate users before allowing them access to servers.
-
Service Aware- With this feature, the load balancer checks the availability status of a server before sending traffic to it.
SSL Offloading is not supported in Exchange 2013 update 7/4/2014
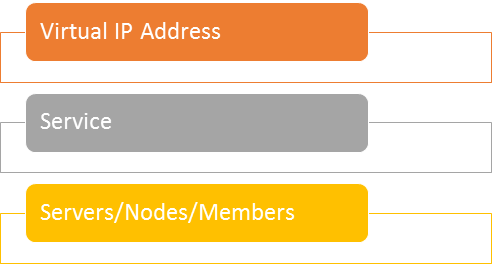
Essential Components
Service has its own Persistence settings, Distribution Settings, Time Out Settings and SSL Offloading settings. Multiple services can be configured in the load balancer to publish the exchange services. Virtual IP Address (VIP) is attached to the service. Each service will have a unique VIP. It is through this VIP that applications connect to its attached service. Behind the service are the Server/Nodes/Members. These can be given to more than one service.
Principals
We shall now look into the different principles involved in Load Balancer in Exchange 2013.
Persistence / Affinity / Stickiness
Since there are multiple servers available when using load balancer, traffic may not always be sent to the same server which will result in increased network traffic. But to avoid this, persistence is used in load balancer which ensures that traffic is sent to the same server.
Different Types of Persistence Are:
-
Source IP
-
HTTP Cookie
-
SSL ID
-
Hash Persistence
In Source IP, persistence is based on the source IP address.
In HTTP Cookie based persistence, an http cookie is generated to track the server by identifying the session.
In SSL ID based persistence, an SSL ID is used to track the session.
In Hash Persistence a Hash is used to track the server.
Distribution
Load balancing of traffic among servers is done by distribution. Different types of distribution are:
-
Round Robin- It uses basic round robin technique to choose the server.
-
Weighted Round Robin- In weighted round robin, the weight pulled on the server is also considered while performing round robin calculations.
-
Least Connections- It routes the traffic to the server with least connections. This mechanism however shows issues while rebooting the cache server as cache server will use many connections while rebooting.
-
Least Response Time- It routes traffic to the server with quickest response time.
SSL Offloading
Through SSL offloading, the load balancers will re-crypt/decrypt the SSL traffic from clients. This thus offloads the task of decryption/re-cryption from the application server saving essential application server resources. Thus the CAS is now free from performing decryption and encryption, hence freeing considerable amount of processor utilization from it. Also, SSL can be applied between Load Balancer and Exchange. Here, exchange will send SSL encrypted data to load balancer. Load balancer encrypts it, re crypts it and sends it to exchange. And finally system without Offloading only permits 2 types of persistence- Source IP and SSL Session whereas a system with SSL Offloading permits all persistence schemes.
Layer 4
Layer 4 is the external network layer. It works on the data in the network and transport layer. They require lesser resources and have a better performance.
Layer 7
Layer 7 acts in the application layer of the server model. It is application aware, requiring decryption of the traffic.
Routing Options
-
Source Address Network Translation (SNAT)
The Source address of the incoming packet is modified. The IP address of the client is hidden. This however poises issues while trouble shooting.
-
Load Balancer Default Gateway
In this technique, the default gateway of the server is pointed to the VIP of load balancer.
-
Direct Server Return
In this schema, all incoming requests are passed through the load balancer. This requires a local loopback interface on server, which does not answer to ARP requests. The loopback interface is configured with the VIP of the load balancer.
Possible Configurations
-
One Armed
In ONE ARMED configurations both clients/servers and VIP are housed in the same subnet. The available routing options are:
-
SNAT
-
Direct Server Return
-
-
Two Armed
A two armed configuration requires 2 networks and separate VLAN for each exchange servers. The routing options available are:
-
Load Balancer Default Gateway
-
Direct Server Return.
-
What’s New In Exchange 2013 Load balancing
-
Session Affinity No Longer required
-
SSL Offloading not supported
-
Layer 7 Load balancing no longer required
-
Only CAS needs to be load balanced
-
Health Check for Workloads
Features Retained
Can load balance same workloads
Available Configurations
-
Single VIP
In single VIP a single VIP is used to publish all protocols and they share the same settings. Layer 7 of the network model will be used to find out the destination.
-
Multiple VIP
A separate VIP can be assigned to each protocol. Each protocol can hence be assigned specific settings.
While single VIP is easier to configure as it has only one rule, features like scale out and scale up, logging options, client traffic segmentation are not available in single VIP. Multiple VIP has all these features and enhanced persistence capabilities and multiple availability protocols. But it requires multiple IP address.
Ratish Nair
Microsoft MVP | Exchange Server
Team @ MSExchangeGuru



June 8th, 2013 at 8:00 am
[…] Load Balancing Exchange Server 2013 – Good to know stuff – […]
June 8th, 2013 at 8:08 am
[…] Load Balancing Exchange Server 2013 – Good to know stuff – […]
June 10th, 2013 at 7:52 am
[…] Load Balancing Exchange Server 2013 […]
June 12th, 2013 at 6:03 pm
There are several benefits of enabling SSL offloading when using a hardware load balancer (HLB). When you enable SSL offloading you terminate the incoming SSL connections on the HLB instead of on the CAS servers. By doing so you move the SSL workload (encryption and decryption tasks) which are CPU intensive from the CAS servers to the HLB device(s). With CAS servers getting more and more responsibility with the introduction of new features such as MailTips, Move Request Service (MRS) and because it now also is the endpoint for MAPI clients, it makes even more sense to let the HLB take care of the SSL workload compared to earlier versions of Exchange Server.
July 19th, 2013 at 5:23 am
hey,
can we use windows 2012 NLB for exchange 2013 ?
Regards
sajid
July 27th, 2013 at 12:18 am
Windows NLB isnt preferred to be honest…
Look at the limitations and make a business decision.
Windows Network Load Balancing: http://technet.microsoft.com/en-us/library/jj898588(v=exchg.150).aspx
July 29th, 2013 at 3:18 pm
[…] Load Balancing Exchange Server 2013 – Good to know stuff: https://msexchangeguru.com/2013/06/05/load-balancing/ Public Folders Migration from Exchange 2007/2010 to Exchange 2013: […]
November 4th, 2013 at 10:58 pm
Interesting that as of November 2013, SSL offloading (for Exchange 2013) is still not supported on NetScalers, according to official documentation published October 2013…
April 9th, 2014 at 8:24 am
Hello all,
Can some one please share the steps to configure CAS Server load balancing.
Thanks,
April 9th, 2014 at 10:32 pm
@Rani,
Please feel free to post your issues here:
http://social.technet.microsoft.com/Forums/exchange/en-US/home?forum=exchangesvrdeploy
Then share the link to us and we will answer the concerns as and when we will have time. This will have more people visibility. The best thing is you may get answers from someone else if we are busy.
Regarding you current concern check the below mentioned blog if you don’t want to invest in load balancer. The other option is windows NLB which is explain here.
https://msexchangeguru.com/2013/08/14/windowsnlb/
July 3rd, 2014 at 6:32 am
SSL Offloading is now supported from Exchange 2013 SP1 (CU4).
July 4th, 2014 at 11:31 pm
@DAK
Thank you for pointer.
This is a blog which was written post the release of CU1 in year 2013 so we had highlighted SSL offloading is not supported.
I have updated couple of lines. Please read new blogs for latest info and changes.
I hope rest of the blogs are helping you in finding you goal.
Happy Reading and visiting us.
October 10th, 2014 at 4:55 pm
What are the recommended hardware load balancers? I have had poor experience with one brand and what to move forward with another. Exchange 2013 1200 users.
October 25th, 2014 at 4:02 pm
Hey Greg,
Hope things are well there.
I can understand. I would recommend to go for the best when you are managing critical customers. The best load balancer is F5 but it is costly. http://www.f5.com/it-management/solutions/load-balancing/overview/
I would recommend a hardware LB in compare to virtual which will have its own hardware to process the load.
Feel free to let me know if you need me to connect with F5 team.
December 31st, 2014 at 3:47 pm
Hey there
You mention that multiple VIP will requires multiple IP address.
But as per my understanding that we can use one IP address and assign this IP to each record
Please correct me if i am wrong.
June 9th, 2016 at 10:14 pm
We have a situation were when we put a exchange server into maintenance mode traffic is still sent to the server by the vip. So we need to mark the server as disabled on the vip so traffic isn’t sent to it. Is this normal behavior or is there something that we need to have changed on the vip?
June 13th, 2016 at 3:31 am
I would wonder why wouldn’t you follow our patching blogs mentioned below.
Exchange 2013/2016 – https://msexchangeguru.com/2015/12/26/exchange-update-deployment-process/
Exchange 2010 – https://msexchangeguru.com/2013/05/10/e2010-dag-patching/
June 13th, 2016 at 8:41 am
Thanks for the response.
We are doing pretty much what is suggested in the patching blog. The one thing we don’t do is restart the transprot services. See below. This is the script that is run.
NOTES
Written by Justin Beeden
V2.0 11.16.2013
2.0 Added logic to confirm DAG File Share Witness is operational to maintain quorum
Added logic to confirm QueueTargetFQDN is a FQDN, will attempt to resolve to FQDN if hostname is entered
Added logic to confirm mail queues have been moved to QueueTargetFQDN
Added logic to confirm all active database copies have been moved to another DAG member
1.1 Corrected Spelling error in one of the parameters
1.0 Initial
.SYNOPSIS
Puts Exchange 2013 DAG nodes into maintenance mode.
.DESCRIPTION
Puts Exchange 2013 DAG nodes into maintenance mode.
http://technet.microsoft.com/en-us/library/dd298065%28v=exchg.150%29.aspx#Pm
.PARAMETER Server
Specifies the DAG node Server name to be put into maintenance mode.
.PARAMETER QueueTargetFQDN
Specifies the target Exchange 2013 mailbox server FQDN to move the mail queue to from the Server to be put into maintenance mode.
.EXAMPLE
PS> .\Start2013DagServerMaintenance.ps1 -Server Server1 -QueueTargetFQDN Server2.contoso.com
Puts Server1 into maintenace mode and moves all queued mail to Server2 for delivery
#>
#Requires -version 3.0
[CmdletBinding()]
Param(
[Parameter(Position=0, Mandatory = $true,
HelpMessage=”Enter the name of the DAG Server to put into Maintenance mode.”)]
[string]$Server,
[Parameter(Position=1, Mandatory = $true,
HelpMessage=”Enter FQDN of server to move mail queue to.”)]
[string]$QueueTargetFQDN
)
Begin
{
try{
#If QueueTargetFQDN is not enterend as a FQDN will attempt to resolve it to a FQDN
$TargetServer = ([System.Net.Dns]::GetHostByName($QueueTargetFQDN)).Hostname
}
catch{
#If above does not resolve to a valid FQDN script will throw error and quit script
Throw “Could not resolve ServerFQDN: $QueueTargetFQDN hostname needs to be resolvable FQDN.”}
}
Process
{
#Function to check all transport queues except Poison and Shadow queues are empty
function CheckQueues(){
$MessageCount = Get-Queue -Server $Server | Where {$_.Identity -notlike “*\Poison” -and $_.Identity -notlike”*\Shadow\*”} |
Select MessageCount | Where {$_.MessageCount -ne 0}
if($MessageCount){
Write-Host “$Server still has messages in transport queue, will check again in 30 seconds…” -ForegroundColor Yellow
Start-Sleep -s 30
CheckQueues
}
else{
Write-Host “Transport queues are empty.” -ForegroundColor Green
}
}
#Function to check all active database copies have been moved to another member of the DAG
function CheckActiveDatabase(){
$ActiveDatabase = Get-MailboxDatabaseCopyStatus -Server $Server | Where {$_.Status -eq ‘Mounted’}
if($ActiveDatabase){
Write-Host “$Server is still hosting active database copies, will check again in 30 seconds…” -ForegroundColor Yellow
Start-Sleep -s 30
CheckActiveDatabase
}
else{
Write-Host “All active database copies have been moved.” -ForegroundColor Green
}
}
#Function to check on DAGs File Share Witness if needed by DAG
function CheckFSW(){
$FSW = Get-DatabaseAvailabilityGroup -Identity $Server.DatabaseAvailabilityGroup -Status | Where {$_.WitnessShareInUse -eq ‘InvalidConfiguration’}
if($FSW){
Throw “There is an issue with this DAGs File Share Witness, fix BEFORE doing node maintenance.”
}
else{
Write-Host “DAG File Share Witness OK or not in use.” -ForegroundColor Green
}
}
Write-Verbose “Checking DAG File Share Witness”
CheckFSW
Write-Verbose “Begining the process of draining the transport queues”
Set-ServerComponentState $Server -Component HubTransport -State Draining -Requester Maintenance
Write-verbose “Begining the process of draining all Unified Messaging calls”
Set-ServerComponentState $Server -Component UMCallRouter –State Draining –Requester Maintenance
Write-Verbose “Redirecting messages pending delivery in the local queues to $QueueTargetFQDN”
Redirect-Message -Server $Server -Target $TargetServer -Confirm:$false
Write-Verbose “Pausing the cluster node, which prevents the node from being and becoming the PrimaryActiveManager”
Suspend-ClusterNode $Server
Write-Verbose “Moving all active databases currently hosted on $Server to other DAG members”
Set-MailboxServer $Server -DatabaseCopyActivationDisabledAndMoveNow $True
Write-Verbose “Preventing $Server from hosting active database copies”
Set-MailboxServer $Server -DatabaseCopyAutoActivationPolicy Blocked
Write-Verbose “Placing $Server into maintenance mode”
Set-ServerComponentState $Server -Component ServerWideOffline -State Inactive -Requester Maintenance
}
End
{
CheckQueues
CheckActiveDatabase
Write-Host “$Server is fully in maintenance mode and ready for maintenance.” -ForegroundColor Green