Exchange 2016: Deny External Access to EAC
Security has been the key with this growing cyber-attack world. So my customer asked to block external ECP access. Here is how we implemented this.
We have following options and my views on it.
- Block at the url https://url/ECP at the Firewall or Load Balancer level
This sounds a good option except not every firewall or load balancer do it. We also need to involve network team.
- Block the AdminEnabled in the ECP Virtual Directory property.
This is new feature but this block internal access as well. So not a nice option. The following cmdlet can be used to apply this.
Set-ECPVirtualDirectory -Identity “Servername\ecp (default web site)” -AdminEnabled $false
- Block the AdminEnabled in the ECP Virtual Directory property with new server which will be used for ECP access.
Adding another server which will use some hardware resources in virtualized setup or a new hardware server + Windows and Exchange License cost to access ECP is never a recommendation. At the same time, it gives you full isolation.
- Remove External URL on the ECP Virtual Directory
Removing Externalurl does not stop the external access unless we also block OWA. So this is not an option.
- Allow only LAN IP Address range on the ECP Virtual Directory from IIS Manager.
Allow only the LAN IP address range sounds a reasonable option to me. Here is how we configure this.
Step 1. Login to your Exchange server and Open IIS Manager
Step 2. Browse down to “Default Web Site” à ECP
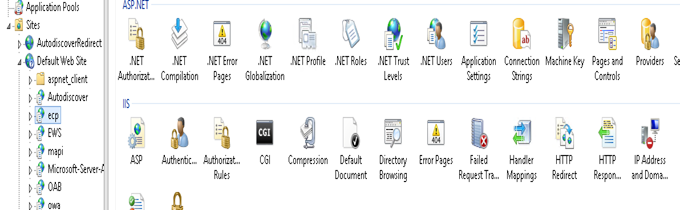
Step 3. Double click on “IP Address and Domain Restrictions”
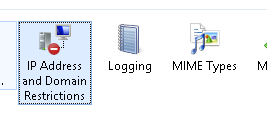
Step 4. Click on “Add Allow Entry”
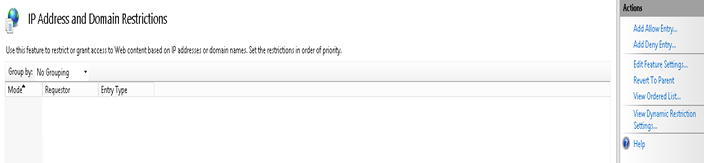
Step 5. Add IP or Range then click Ok

It is not done yet. So have some patience
Step 6. Click on “Edit Feature Settings”

Step 7. In “Access for Unspecified clients” Select Deny and in “Deny Action Type” we can “Not Found” or any other option.
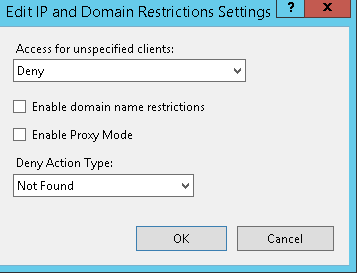
Step 8. Do the IIS reset.
Now we are done. Only the assigned IP Range users can see it.
Are you concerned if your users can still access options which used to take the user to /ecp vdir to get the out of office and other options?
This has changed in Exchange 2016. In Exchange 2016 Options will use the following url and not https://url/ECP
So if you are on Exchange 2013 then do not follow this blog until you see the users option url change in Exchange 2013.
In Exchange 2016 Options will take us to the following url.
https://mail.domain.com/owa/#path=/options/mail
Microsoft MVP | Office Servers and Services
Team@MSExchangeGuru



November 11th, 2016 at 2:15 pm
> Block at the url https://url/ECP at the Firewall or Load Balancer level
> This sounds a good option except not every firewall or load balancer do it. We also need to involve network team
In an environment where the network team is also the e-mail team, is this a better option? I can choose to not publish /ecp/ externally.
—
November 16th, 2016 at 2:26 pm
Yes.
you should be able to block the connections coming with the headers with /ecp on your firewall. At the same time, IP-based blocking is safe as well.
July 7th, 2017 at 9:14 am
This works for OWA as well right?
July 7th, 2017 at 10:39 am
Yes, it should
September 20th, 2017 at 10:43 am
Do these same steps for restricting the ECP website by IP also apply to Exchange 2013?
September 20th, 2017 at 12:39 pm
No.
October 6th, 2017 at 7:45 pm
Would the Set-ECPVirtualDirectory -Identity “Servername\ecp (default web site)” -AdminEnabled $false in exchange 2013 disable the user access into option? Thx
October 6th, 2017 at 11:25 pm
I would suggest to try the option in the lab or even in production. You can always revert back. Overall few minutes task.
October 24th, 2017 at 3:32 am
Please let me know if I can restrict ECP to domain admin (Exchange Administrator) and not for domain users. Domain user access to ECP is not harmful. Thank you in advance and best regards
October 24th, 2017 at 3:49 am
This is for E2016 where domain users do not require ECP.